Web Servers
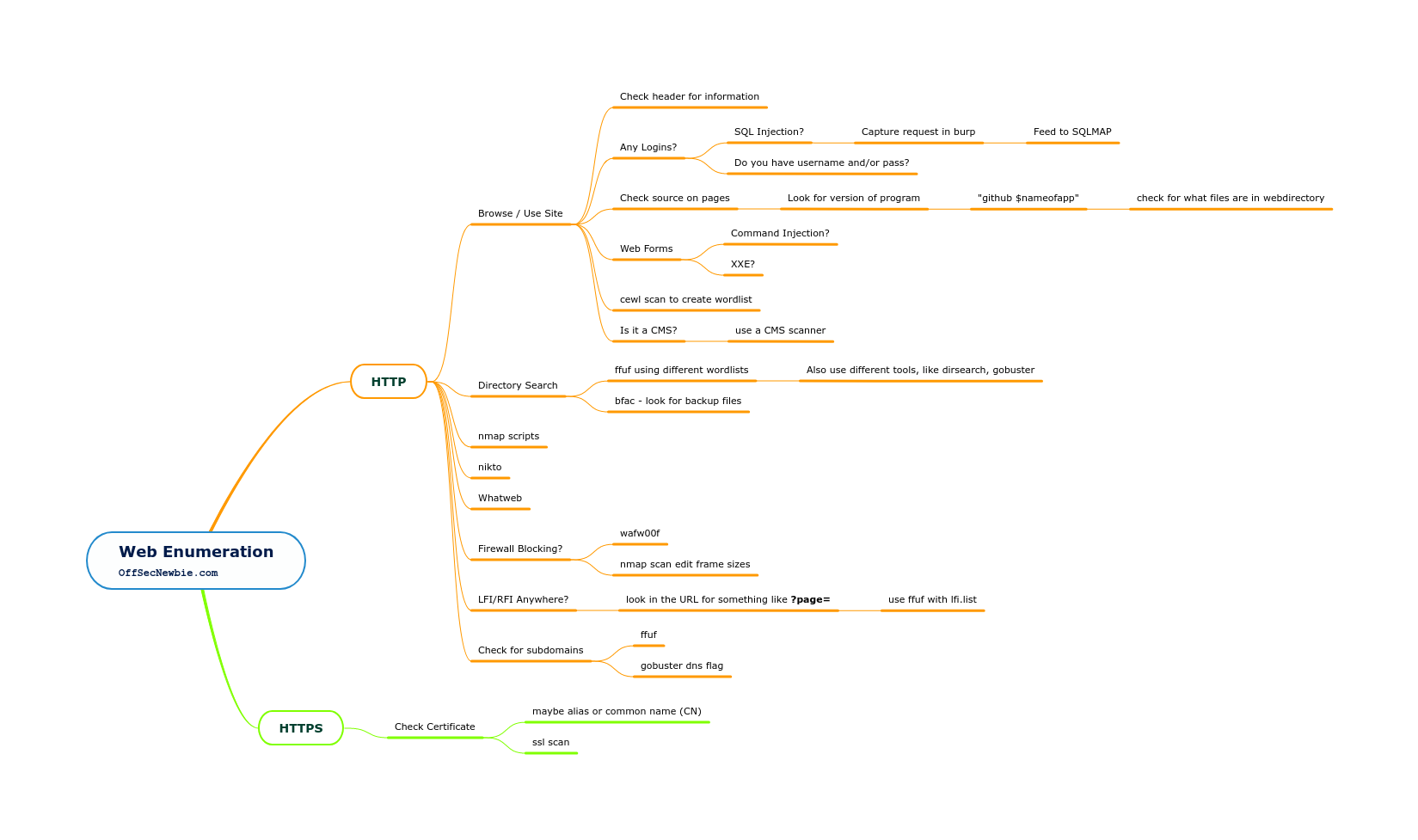
Web Servers
Two most common Apache, Microsoft IIS
Nikto
Run early, its slow but good
Sanity Check
Look at robots.txt
Look in the webpage for comments
Is the site not rendering right? (check dns /etc/hosts)
DIRB
Comes with a default word list
Custom wordlist:
-nwill stop the scan on current dir and move to the next-qstops the running scan and saves the current state-rwill return the remaining scan statistics
Dirbuster
Wordlist location:
To run, set the target to the target url, set the number of threads, select a word list and hit the start button.
Much faster because its multi threaded
Netcat
We can grab the banner of the web service running on the target host:
Enter this HTTP request on the next line
To retrieve the top level page on the webserver we can use the following command:
Run this HTTP request
GoBuster
Another good web application scanner.
dirto run it in directory enumeration mode-ufollowed by the url-wto specify a wordlist
Syntax
dir-> Directory/File Brute force modedns-> DNS brute forcing mode-x-> Flag for extentions to be tested against-w-> Sets a wordlist to be used-U-> Set username for basic authentication (if required by the directory)-P-> Set password for basic authentication-s-> Set the status codes gobuster will recognize as valid-k-> Skip ssl certificate validation-a-> Set a user agent string-H-> Specify and HTTP header-u-> Set the url to brute force/usr/share/wordlists-> Location of the wordlists
Example full syntax
This command tests the /secret/ directory
It specifies to use the wordlist
directory-list-2.3-medium.txtWith the
-xflag it sets gobuster to test for.txtfile extensions i.e. admin.txt, secret.txt
Gobuster Sub-Domain Enumeration
Dirsearch
Full Syntax
WpScan
if you have a wordpress server check below URI as if it is enabled, you can get alot of information.
TLDR; The best one liner
Ideal for wordpress sites to find their vulnerable plugins, users, and themes.
Default scan runs non intrusive checks which means no accounts will be brute forced and themes and plugins will be enumerated passively.
Active enumeration
p->scans popular plugins onlyvt->scans vulnerable these onlyat->scans all themesFull command:
The following command will test a target for all popular plugins:
To scan a wordpress installation only for vulnerable plugins we can run the following command:
Scan for all plugins in the WPScan database run the enumerate option with ap:
Enumerating WP users
Wordpress Bruteforce
can brute force with
wpscanhowever this tool works great
BFAC
Advanced backup-file artifacts for testing web applications
https://github.com/mazen160/bfac
Install
Find backup files on the website/application
If you manage to download a backupfile, grep for users - might be a password as well
Burp Spider Website
Set Foxy Proxy to 127.0.0.1 8080 and enable it
Turn off intercept
Refresh the page you want to spider
Navigate to
Target/Site MapinBurp Suite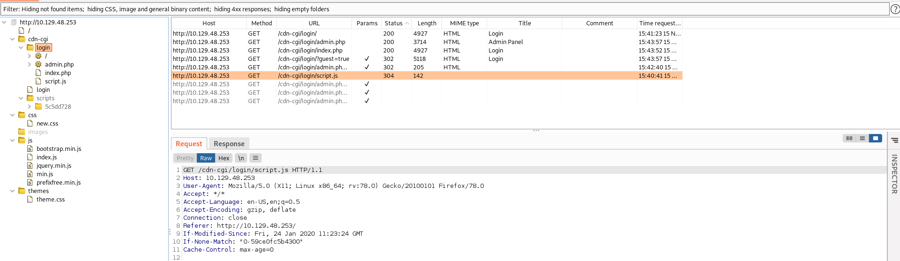
Last updated