Powershell Empire
Overview
Install
Installing Empire
Non Kali OS
git clone --recursive https://github.com/BC-SECURITY/Empire.git
cd Empire
./setup/checkout-latest-tag.sh
sudo ./setup/install.shKali OS
sudo apt install powershell-empireInstalling Starkiller
Once Empire is installed we can install the GUI for Empire known as Starkiller.
cd /optDownload an up to date version of Starkiller from the BC-Security Github repo - https://github.com/BC-SECURITY/Starkiller/releases
chmod +x starkiller-0.0.0.AppImageStarting Empire
Once both Empire and Starkiller are installed we can start both servers. Being by starting Empire with the instructions below.
Starting Starkiller
Once Empire is started follow the instructions below to start Starkiller.
Login to Starkiller
Default Credentials
Uri:
127.0.0.1:1337User:
empireadminPass:
password123
Delete Stale Listeners
If you exit empire without disabling or killing all your listeners next time you start empire it will still show and not let you disable or kill it
open this file in a database browser
Server Obsfucation
Change
Invoke-EmpiretoInvoke-RandomStringHerein these files:
Listeners Overview
http- This is the standard listener that utilizes HTTP to listen on a specific port.http_com- Uses the standard HTTP listener with an IE COM object.http_foreign- Used to point to a different Empire server.http_hop- Used for creating an external redirector using PHP.http_mapi- Uses the standard HTTP listener with a MAPI COM object.The next five commands all use variations of built out services or have unique features that make them different from other listeners.
meterpreter- Used to listen for Metasploit stagers.onedrive- Utilizes OneDrive as the listening platform.redirector- Used for creating pivots in a network.dbx- Utilizes Dropbox as the listening platform.http_malleable- Used alongside the malleable C2 profiles from BC-Security.
Creating a Listener
Configure your listener, the only two options you will need to change are the host IP and the host port.
HTTP listener
Name - Specify what name the listener shows up as in the listener menu.
Host - IP to connect back to.
Port - Port to listen on.
BindIP - IP to bind to (typically localhost / 0.0.0.0)
The following options can be useful for bypassing detection techniques and creating more complex listeners.
DefaultProfile - Will allow you to specify the profile used or User-Agent.
Headers - Since this is an HTTP listener it will specify HTTP headers.
Launcher - What launcher to use for the listener this will be prefixed on the stager.
Stagers Overview
The stager is similar to a payload or reverse-shell that you would send to the target to get an agent back.
Empire has multiple parts to each stage to help identify each one. First is the platform this can include multi, OSx, and Windows. Second the stager type itself / launcher.
multi/launcher- A fairly universal stager that can be used for a variety of devices.windows/launcher_bat- Windows Batch filemulti/bash- Basic Bash StagerYou can also use stagers for more specific applications similar to the listeners. These can be anything from macro code to ducky code for USB attacks.
windows/ducky- Ducky script for the USB Rubber Ducky for physical USB attacks.windows/hta- HTA server an HTML application protocol that can be used to evade AV.osx/applescript- Stager in AppleScript: Apple's own programming language.osx/teensy- Similar to the rubber ducky is a small form factor micro-controller for physical attacks.
Generating a Stager
Set the listener to the one you made in the previous task
The stager menu can come with various options depending on the stager selected as well as optional fields.
Base64- Enable or disable stager encoding with base64.SafeChecks- Enable or disable checks for the stager.Some of the optional fields include
ASMIBypass,Obfuscate,ETWBypass, etc.
Agents Overview
Agents are used within Starkiller similar to how you would interact with a normal shell or terminal.
Agents are color-coded and use icons to help distinguish Agent status. Below is an outline of the color and icon scheme
Red- User is no longer respondingBlack- User is responding normallyUser Icon- Normal user accountUser Icon w/ Gear- System user account
Using Agents
Below you can see the basic layout of the Agent interaction menu and what capabilities an agent on a device has.
Module Overview
Modules are used in Empire as a way of packaging tools and exploits to be easily used with agents.
We can take a look at a few useful ones for enumeration and privilege escalation outlined below:
Empire sorts the modules by the language used: PowerShell, python, external, and exfiltration as well as categories for modules you can find the categories below.
Using Modules
Modules require no, to very little configuration
Below you can see the task to run Seatbelt being assigned then the output of the module being printed to the console window.
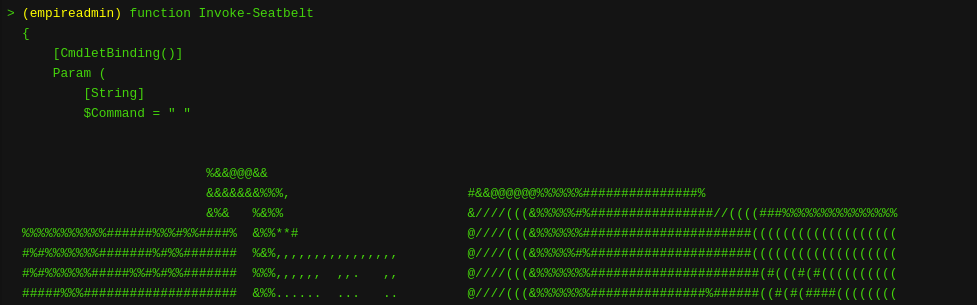
Because all modules are run remotely from a task and agent this means that we do not have to worry about Anti-Virus or other possible detections.
Plugins Overview
Plugins are an extension of the base set of modules that Empire comes with. You can easily download and use community-made plugins to extend the use of Empire.
To use a plugin, transfer a plugin.py file to the /plugins directory of Empire. As an example of how to use plugins, we will be using the socks server plugin made by BC-Security, you can download it here.
Using Plugins
Transfer or clone the plugin that you want to use into the plugins directory for Empire.
After Empire version 3.4.0, Empire automatically loads plugins into the server. If the plugin is not already running you - Can use the plugin command to load the plugin for use.
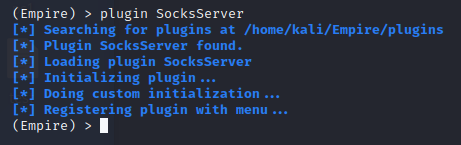
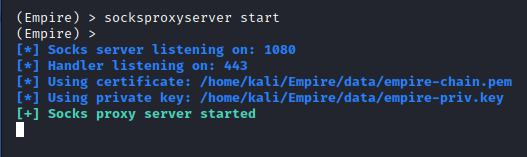
You can run plugins using the start and stop commands. Depending on the plugin the flags / parameters can change for each.
Great Modules for AD
Get the SPNs from LDAP output or from bloodhound
Empire Agent Obfuscation / Meterpreter/Empire Tandem
This assumes an active meterpreter session on a remote host
AMSI Bypass
Empire Internal Host Scanning
Empire PSInject Agent into another process
Empire Registry Persistence
Empire AS-REP Roast
Last updated