SSH Tunneling and Port Forwarding
SSH -D
SOCKS Proxy Tunneling
Enable Dynamic Port Forwarding with SSH
ssh -D 9050 [email protected]Edit /etc/proxychains.conf with Port to Use
socks4 127.0.0.1 9050Scan Remote Network from Target Machine Over SSH Tunnel
proxychains nmap -v -sn 172.16.5.1-200Only a full TCP connect scan works over proxychains
Windows may not respond to a normal ping as well so use -Pn
proxychains nmap -v -Pn -sT 172.16.5.19Metasploit with Proxychains
proxychains msfconsole
set LHOST eth0
search rdp_scanner
use 0
set rhosts 172.16.5.19
runxfreerdp with Proxychains
Forward Connections
Creating a forward (or "local") SSH tunnel can be done from our attacking box when we have SSH access to the target.
There are two ways to create a forward SSH tunnel using the SSH client -- port forwarding, and creating a proxy.
Port forwarding is accomplished with the
-Lswitch, which creates a link to a Local port. For example, if we had SSH access to172.16.0.5and there's a webserver running on172.16.0.10, we could use this command to create a link to the server on172.16.0.10:
We could then access the website on
172.16.0.10(through172.16.0.5) by navigating to port8000on our own attacking machine.For example, by entering
localhost:8000into a web browser.Using this technique we have effectively created a tunnel between port
80on the target server, and port8000on our own box. Note that it's good practice to use a high port, out of the way, for the local connection.This also means that we do not need to use
sudoto create the connection. The-fNcombined switch does two things:-fbackgrounds the shell immediately so that we have our own terminal back.-Ntells SSH that it doesn't need to execute any commands -- only set up the connection.
Proxies
These are made using the
-Dswitch, for example:-D 1337. This will open up port1337on your attacking box as a proxy to send data through into the protected network. This is useful when combined with a tool such asproxychains.An example of this command would be:
This again uses the -fN switches to background the shell. The choice of port 1337 is completely arbitrary -- all that matters is that the port is available and correctly set up in your proxychains (or equivalent) configuration file. Having this proxy set up would allow us to route all of our traffic through into the target network.
Reverse Connections
Reverse connections are very possible with the SSH client (and indeed may be preferable if you have a shell on the compromised server, but not SSH access).
They are, however, riskier as you inherently must access your attacking machine from the target
Make it safe
First, generate a new set of SSH keys and store them somewhere safe
ssh-keygenCopy the contents of the public key (the file ending with .pub), then edit the ~/.ssh/authorized_keys file on your own attacking machine. You may need to create the ~/.ssh directory and authorized_keys file first.
On a new line, type the following line, then paste in the public key:
This makes sure that the key can only be used for port forwarding, disallowing the ability to gain a shell on your attacking machine.
The final entry in the authorized_keys file should look something like this:
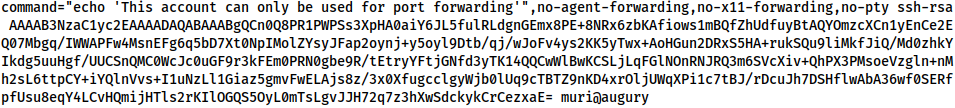
Next. check if the SSH server on your attacking machine is running:
The only thing left is to do the unthinkable: transfer the private key to the target box.
With the key transferred, we can then connect back with a reverse port forward using the following command:
To put that into the context of our fictitious IPs:
172.16.0.10and172.16.0.5, if we have a shell on172.16.0.5and want to give our attacking box (172.16.0.20) access to the webserver on172.16.0.10, we could use this command on the172.16.0.5machine:
This would open up a port forward to our Kali box, allowing us to access the
172.16.0.10webserver, in exactly the same way as with the forward connection we made before!
Examples
If you wanted to set up a reverse portforward from port
22of a remote machine (172.16.0.100) to port2222of your local machine (172.16.0.200), using a keyfile calledid_rsaand backgrounding the shell, what command would you use? (Assume your username is "kali")
What command would you use to set up a forward proxy on port
8000to[email protected], backgrounding the shell?
If you had SSH access to a server (
172.16.0.50) with a webserver running internally on port80(i.e. only accessible to the server itself on127.0.0.1:80), how would you forward it to port8000on your attacking machine? Assume the username isuser, and background the shell.
Fixing SSH tunnels that only listen on loopback
if you run into a situation where you are attempting to tunnel and instead of
0.0.0.0the device only listens on127.0.0.1you have two choicesif root
or utilize socat
above command listens on
0.0.0.0:80and will port bend the connection to127.0.0.1:8080when it is assumed you have your reverse tunnel set up back to kali station
Last updated