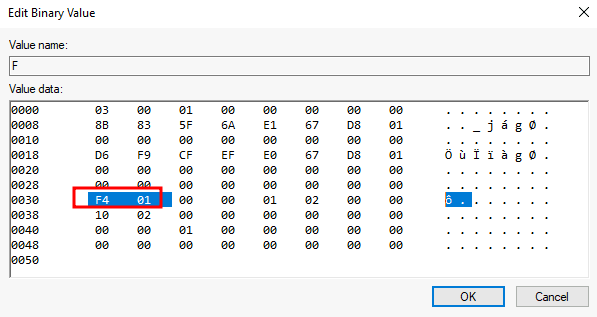
RID Hijacking
Overview
wmic useraccount get name,sid
Name SID
Administrator S-1-5-21-1966530601-3185510712-10604624-500
DefaultAccount S-1-5-21-1966530601-3185510712-10604624-503
--snip--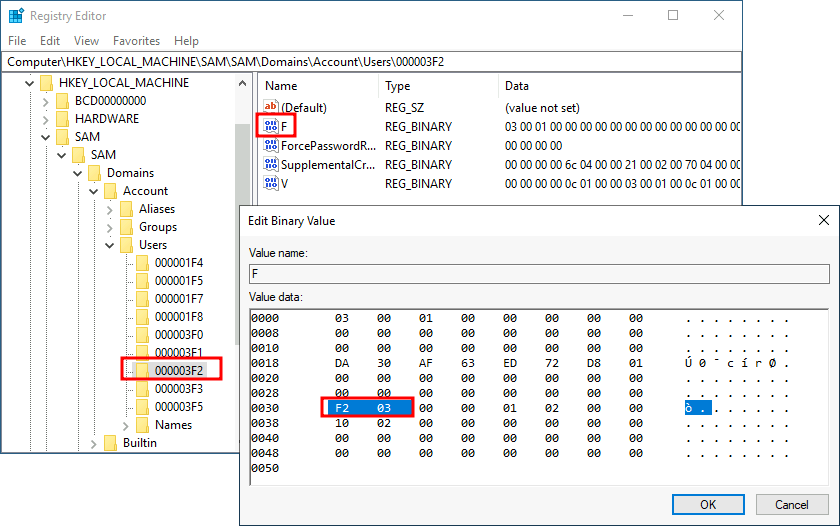
Last updated
wmic useraccount get name,sid
Name SID
Administrator S-1-5-21-1966530601-3185510712-10604624-500
DefaultAccount S-1-5-21-1966530601-3185510712-10604624-503
--snip--

Last updated