powershell-cheatsheet
Powershell
Powershell Downgrade Attack
powershell.exe -Version 2.0 -NoLogo -NoProfileResources
Basic Enumeration
Hotfixes
Creating Objects From Previous cmdlets
Checking the Stopped Processes
Sort Object
Find File Recursive
See all Cmdlets Installed
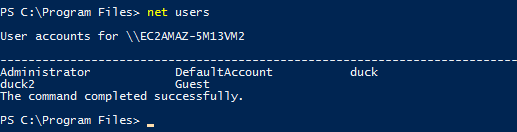
Users
Groups
IP Address Information / TCP/UDP Connections
Base64 Powershell Decode
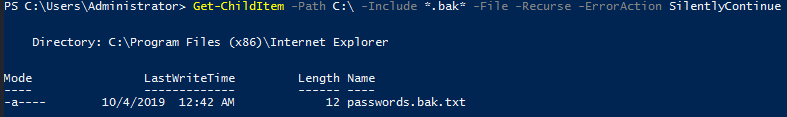
Find backup Files
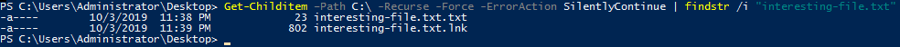
Find specific string inside a file
Services and Processes
Scheduled Tasks
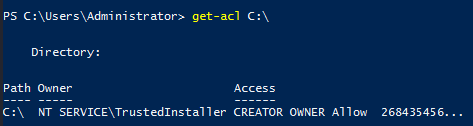
See Owner and Access
Scanners
Last updated